Building an AppSec Program can be a challenge. Where do you start, and what should it entail?
September 2, 2022In my previous article, I discussed an AppSec Program and why you should have one. In this article, I will focus on the minimum number of components an AppSec Program should consist of and an easy method to measure its maturity level.
During my 14+ years working in the AppSec industry, I have helped numerous fortune 500 companies build and mature their AppSec Programs. When looking at all these programs, there are 20 common components they all share. I like to refer to the collection, or combination, of these 20 components as the Minimum AppSec Program (MAP).
Minimum AppSec Program (MAP)
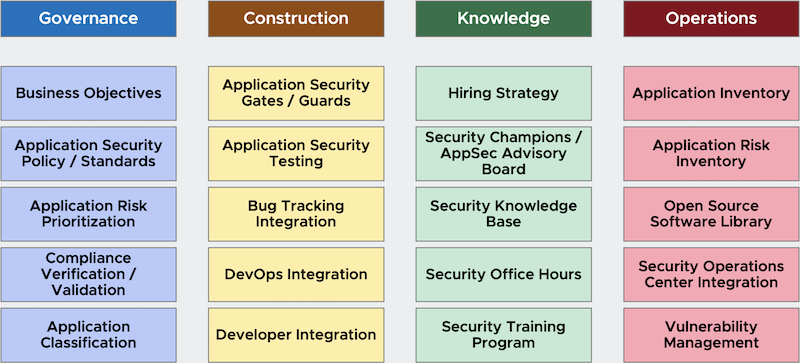
For ease of understanding and consumption, I have divided these 20 components into four categories: Governance, Construction, Knowledge, and Operations (see figure 1 above).
Those who have experience assessing the maturity level of an AppSec Program might see some similarities with OpenSAMM or BSIMM. These are what I would like to call heavy-weight methodologies. The challenge with these methodologies is that you need to have a lot of knowledge of- and experience with- AppSec to use and understand them. Additionally, doing a maturity level assessment with either methodology can take weeks or even months! Unfortunately, you may not have the luxury of that amount of time. You need an AppSec Program now! Using my MAP, you can do a maturity assessment in just a few hours. Let me explain.
Minimum AppSec Program Assessment
First, you need to sit in front of the right people for the job: the person responsible for AppSec (e.g. CISO) and the person in charge of AppDev (e.g. VP of Engineering). For a maturity assessment, I like to ask them five questions per component. These questions and predetermined answers are in layman’s terms. Hence, they do not require a lot of specific AppSec knowledge to be able to understand and use them. Every question has five answers, rated from non-existing (0) to fully implemented (4). By using this Q & A methodology, it is relatively easy to determine the current maturity level of the AppSec Program and where you need to focus your efforts next: the desired level of your entire AppSec Program (see figure 2 below for an example of some possible assessment results).
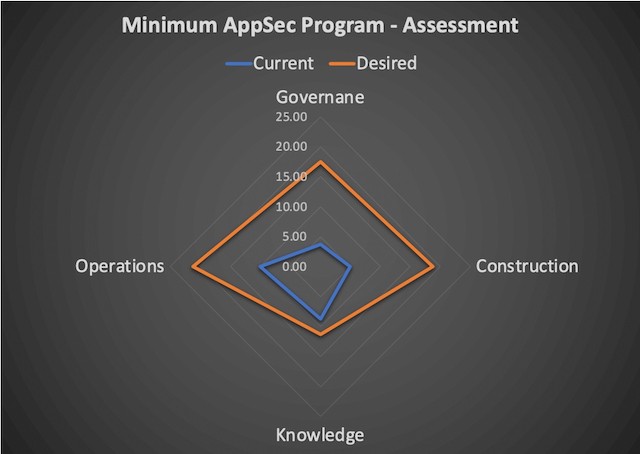
For the sake of this article, I will not go over each question and answer. We can discuss these in a personal session. However, I like to help you get at least a minimal understanding of where you are at with your MAP. So I have listed the 20 components and their meaning below.
Governance:
- Business Objectives: The alignment between your business objectives and your AppSec program.
- Compliance Verification/Validation: Measure, track, and report on application compliance status.
- Application Security Policy/Standards: Specify application development requirements and best practices.
- Application Risk Prioritization: Specify application risk prioritization.
- Application Classification: Specify application classification.
Construction:
- Application Security Gates/Guards: Prevent vulnerable applications from moving from one environment to the next.
- Application Security Testing (AST): Testing early and often for exploitable vulnerabilities throughout the entire SDLC.
- Bug Tracking Integration: Automatically create bugs for high and critical vulnerabilities.
- DevOps Integration: Automatically test for exploitable vulnerabilities in the build pipeline.
- Developer Integration: Test for known vulnerabilities from within the developers’ day-to-day activities.
Knowledge:
- Hiring Strategy: Hire the right people at the right time.
- Security Champions/AppSec Advisory Board: Scale application security advocacy throughout the development organization.
- Security Knowledge Base: Disseminate application security knowledge and collaboration throughout the entire organization.
- Security Office Hours: Recurring meetings where developers/security champions can ask questions/be informed about (emerging) security issues.
- Security Training Program: Train developers on secure software development.
Operations:
- Application Inventory: Track the applications used within the organization.
- Application Risk Inventory: Measure, track, and report on the trend of the risk status of your application portfolio.
- Open Source Software (OSS) Library: Track the usage of OSS across your organization.
- Security Operations Center (SOC) Integration: Detect and prevent the exploitation of vulnerabilities in applications.
- Vulnerability Management: The detection, auditing, and remediation of vulnerabilities.
What’s next?
I trust this article has been of help to you. If you are interested in discussing your AppSec Program or want to perform a maturity assessment using my method, please connect with me. See my contact details below.
Percy Rotteveel - Cell: (650) 421-3631 - eMail percy@rotteveel.ca
Article: https://www.linkedin.com/pulse/how-start-assess-appsec-program-percy-rotteveel/